Keeping Cybersecurity Simple
A step-by-step journey to securing your business
Keeping Cybersecurity Simple
A step-by-step journey to securing your business
Keep Your Business Secure: CyberSmart Security
- Proactive endpoint security management
- Government-standard certified
- Powerful and affordable cybersecurity
- User-centric granular security
- Perfect for SMEs and Freelancers
CyberSmart: What is it and why is it important?
CyberSmart is the starting block on getting your business up to speed with becoming cyber security verified. Essentially, CyberSmart is a program that runs on Windows, Mac, iOS or Android devices. It runs silently in the background, analysing each registered device for its cybersecurity score. The scrutiny placed on these devices follows a standard, where checks are performed to ensure a level of security across your business. Security checks are performed automatically on each device, checking for a standard level of protection. Checks include but are not limited to things like a firewall is enabled, automatic operating system updating is active and password-enabled user access.
CyberSmart as an end user
As an end user, you will hardly know CyberSmart is even active on your device. For the program runs hidden in your device window, accessible on Windows through the hidden icons area on the start bar. Open the chevron in your task bar, and you will see the small icon hiding the checks, training, and policy options.
CyberSmart checks
The list of CyberSmart checks is the same for everyone and easily visible by the end-user. The checks indicate how secure the device you are working from is. The checks within this area show which checks you are failing on and as an end user, are easily fixable with step- by-step guides on how to resolve.
An end user can always work on improving their cybersecurity score. On top, an IT Helpdesk, of which Greenlight Computers provide, can assist with company wide resolutions like group policy deployment.
CyberSmart training
CyberSmart training is great for engaging with your end users to work in a cyber-secure manner. Such training modules are automatically scheduled for your staff, in self-guided training modules on many different aspects of cyber security. It is all well and good having a secure device, but not having the right security conscious mindset could make it all fall apart. The training modules offered through CyberSmart covers things like how to securely back up data or how to have the perfect passwords. The training modules are typically video based with quizzes at the end, so you as a business know who has the right security training. A bonus of the training module is you have a leaderboard to encourage friendly competition within your workplace, so your staff are vying to get to the top and demonstrate they know the best security procedures, which in turns is only a benefit for your business.
CyberSmart policies
A bonus of CyberSmart, is that it can be used as a tool to share documents across your business and have a track record to see who has viewed and acknowledged a document. This is perfect for example, in applying for ISO Accreditation where you need your colleagues to be aware of the policies and procedures your business follows. The CyberSmart policies module works like a PDF reader, where the documents available for viewing are displayed within the app. You must scroll through the documents before a button appears for the end user to agree to the policy.
Contact Us for a more in-depth conversation about the benefits of CyberSmart
CyberSmart as an administrator
We have discussed what CyberSmart is like for an end user, but what about administration? Well, CyberSmart is just as simple to administer, as it is to be the end user.
Smart Score
An administrator of CyberSmart for your business, will have easy access to the visibility of your overarching security with a smart score. The smart score gives you a percentage that indicates the level of security your business has from all the registered devices you have in your CyberSmart portal. This metric, percentage based, averages the security scores that individual devices are achieving, to provide a clean overview of where your business sits currently with its cybersecurity score. We suggest a score over 90% is a great metric to aim for.

How to improve your secure score
As outlined above, the smart score is the overarching metric for your whole business. The percentage calculation averages the security scores from your employee devices. Alongside the smart score percentage score, you will also get prompts from the system, that automatically suggest the steps you must take to achieve the perfect 100.
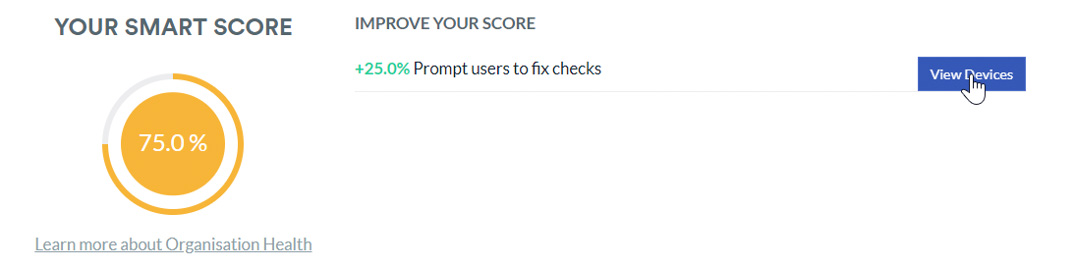
Upon clicking through to see which devices are affected, you will receive a device report that breaks down the number of devices you have registered, and which checks are failing. The simple but effective report outlines which security checks are failing, the name of the device as well as the last user to login.
With security conscious employees, they should be proactively monitoring their own security with the CyberSmart app. But for those that need the nudge, you can follow up with users listed here. Another handy feature, is the manual resolve button. For false-positives, this overriding manual resolve button can tick the failing checks off. Be careful with this though – you’ll only be shooting yourself in the foot by faking your security results!
Company report
We touched upon the company report above, but to go into some extra detail on what to expect from this area…
Export of reports
You can manage all devices registered under your CyberSmart portal within this area – see who has used the machines and extrapolate which devices are missing by comparing against your asset register. You can also export the company output – perfect for extra analysis outside of the web-based interface.
Desktop and mobile security reporting
Being a modern security tool, CyberSmart is available for desktop and mobile devices. Within the portal, you can see which of each type have been registered and which security checks are failing. For a reminder, iOS and Android devices are the supported mobile operating systems.
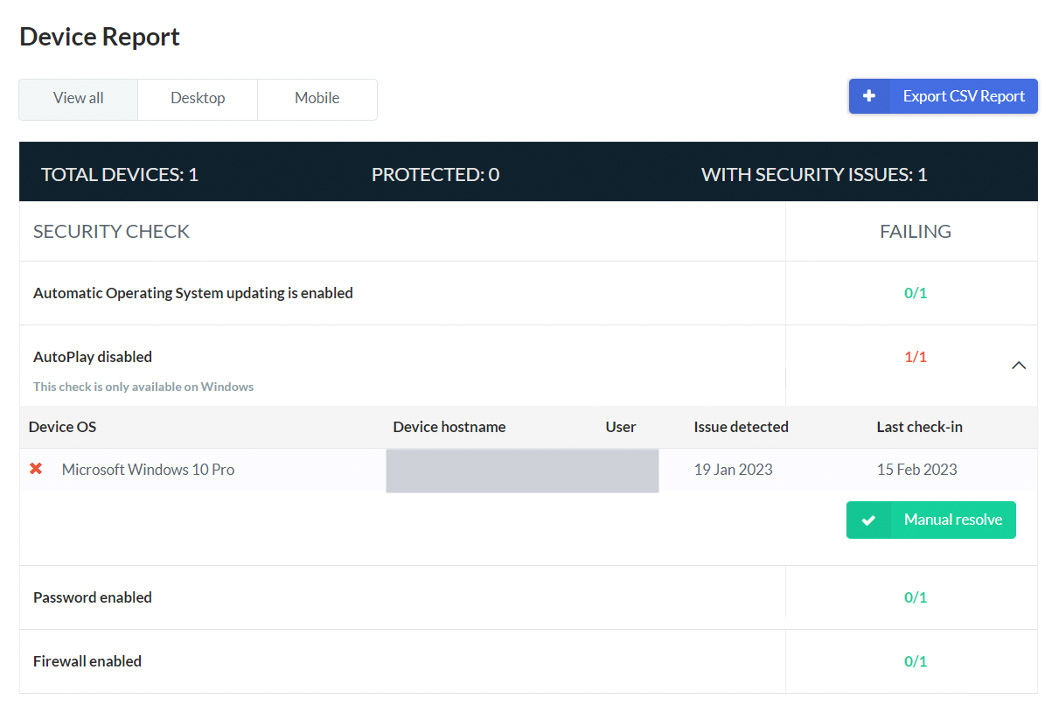
Software vulnerability reporting
One powerful reporting tool from the CyberSmart admin dashboard, is the ability to see which software is installed across your business. While CyberSmart is not a monitoring tool, part of its function is to see which software is installed on your company registered devices. With this function, CyberSmart knows the latest versions of available software and can alert the administrators to which software needs updating across your estate. The software reported back through CyberSmart, shows which have vulnerabilities. On top, it can highlight where people have been installing ‘personal use’ software, like game installs. This can really hone down your cybersecurity as a business, ensuring that company devices are only used as such and the software kept on them, is free from vulnerabilities.
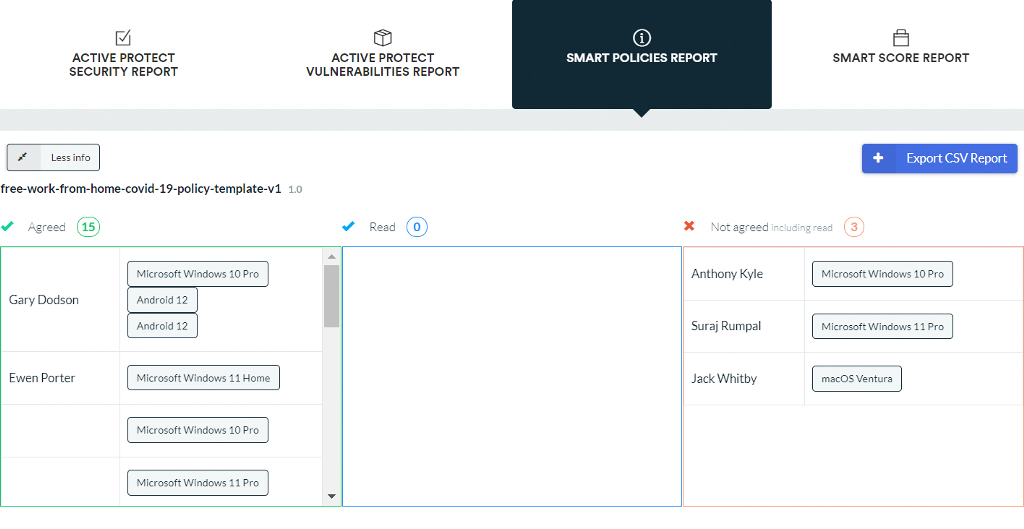
Policy reporting, perfect for ISO Accreditation
One of the last great reporting functions of the CyberSmart admin portal, is to see who has signed the policies that go through their program. A simple, but again effective use of this tool, is to push documents and understand exactly who has read and acknowledged.
The output from CyberSmart provides a great overview of who is following and understanding your policies, and again who needs that prompt to review documents.
Last check in date, last user on the machine
CyberSmart has always been a powerful, simple security solution for SMEs. The background running of the application, as well as how easy it is for end users to improve their own security, makes a difference for small businesses. All too often, businesses only fret about security after they have been breached. The proactive solution that CyberSmart provides comes into its own again with its simplicity on how you can see the last time a device was used and the last user to be on there.
This simple reporting shows which devices may have been left behind and as such, the software on them may be out of date. Exporting these types of reports can show which devices have been forgotten about, or which simply need an IT Technician to resolve connectivity.
Overview cybersecurity training sessions for a business
The modules that come included in a CyberSmart license, include video and other learning material for your users to improve their cybersecurity perceptions. Covering everything from mobile working, to how to backup data, these modules are scheduled in for users to complete. Scheduled through the year, these learning materials help to keep staff encouraged to stay on top of their security, as well as not overloading them with too much distraction from the day to day.
Always available if preferred to attack all the cybersecurity modules at once, these training materials are the same to all colleagues and a leaderboard of who has the best scores is always available through the app to the end users, promoting a healthy competition. As an administrator of the backend of CyberSmart, you get to see who has completed the modules, and their average score.
Dashboard access – who has admin rights and who can see
The backend dashboard for CyberSmart is all managed through a website portal. You can define as a business who you want to be managing your business, and who the automated reports come to. With CyberSmart, its simple and secure, always.
Automatically enrolling domains, so all under same roof.
At Greenlight Computers, we have different sister companies in Greenlight Web and MBH to name two. One of the fab features of CyberSmart, is that we didn’t need to set up a different dashboard portal with different admin controls and rights for these companies. Instead, we could define domains that we’d like to keep under the one roof. It’s a small feature that shows CyberSmart goes above and beyond for its ease of use.
Securing Your Network: Protecting Your Business
Collectively with endpoint security management, you will find that once above the 90% threshold, your business will be in a much better position to confront the threats of cybersecurity. Naturally, this will extend beyond the individual endpoints, to your network also. Deployment of firewalls and global policies will naturally be topics that arise through the suggestions CyberSmart makes in its tool. But the best place to secure your network, is to explore the certification, Cyber Essentials.
Staying CyberSmart: Continuous Monitoring
CyberSmart is continually monitoring your business for cyber threats. Keeping a high smart score across your business will keep your business at a grounded level for your endpoints. The regular reporting that comes to administrator mailboxes, goes that next step for staying on top of the results and changes that naturally change over time. CyberSmart is always updating and coming out with new features to make it the ultimate destination to secure your business. Get in touch with our team to learn more about what CyberSmart can do for you.
Differences between CyberSmart, Cyber Essentials and Cyber Essentials Plus
CyberSmart is what we consider the best foundation to begin your business journey into securing your company. The next step up, is to get Cyber Essentials certified. Watch the video to learn more, but essentially Cyber Essentials is a government certified qualification for your business that means your company operates at the minimum level of security needed for government projects.
Cyber Essentials is a self-guided certification through the CyberSmart portal, that is questionnaire based and goes through everything from network security, device security, group policies and even the security of buildings and backups.
The involved questionnaire can often bring up areas of security you may not have considered prior – but it’s a fantastic certification to have as a business, as it’ll open you up to the public sector.
Where Cyber Essentials differs from Cyber Essentials Plus, is how there is an independent third party in the Plus version, who double checks your answers, fills the Cyber Essentials form with their findings and tries cyberattacks against your business. It is the ultimate certification for proving your cyber security worth.
Contact Us for a more in-depth conversation about the benefits of CyberSmart
